Private Networking with SGA (Public Cloud)
Customers using public cloud infrastructure can create a Frame account using Frame-managed networking, Private Networking with Streaming Gateway Appliance (SGA) so users can access the Frame workload VMs through the SGA. The Internet-accessible SGA serves as a reverse proxy for Frame sessions between the end users and their Frame workload VMs in the private network. The Frame workload VMs only have private IP addresses. For egress from the workload VMs to the Internet, these workload VMs are configured to communicate directly to the Internet through a NAT gateway in the public cloud infrastructure.
If users must access network resources on-premises or in a private network, a private network connection (e.g., VPN, direct connection, SD-WAN, VPC/VNET peering) with the appropriate routing must be implemented.
Customers who choose to create a Frame account in their own managed network where users will access the Frame workload VMs from the Internet through an SGA must follow the networking requirements defined below.
To ensure proper network communication to the Frame Platform there are two Backends available depending on which one should be used for the connection for services and VMs please refer to the corresponding networking requirements:
USE (located in the United states- Location AWS Datacenter Virginia)
DEU ( located in European Union - Location AWS Datacenter Frankfurt)
FRP8 Networking (SGA 4)
FRP8 is a udp-based protocol for all communication between the end user and the Frame workload VMs.
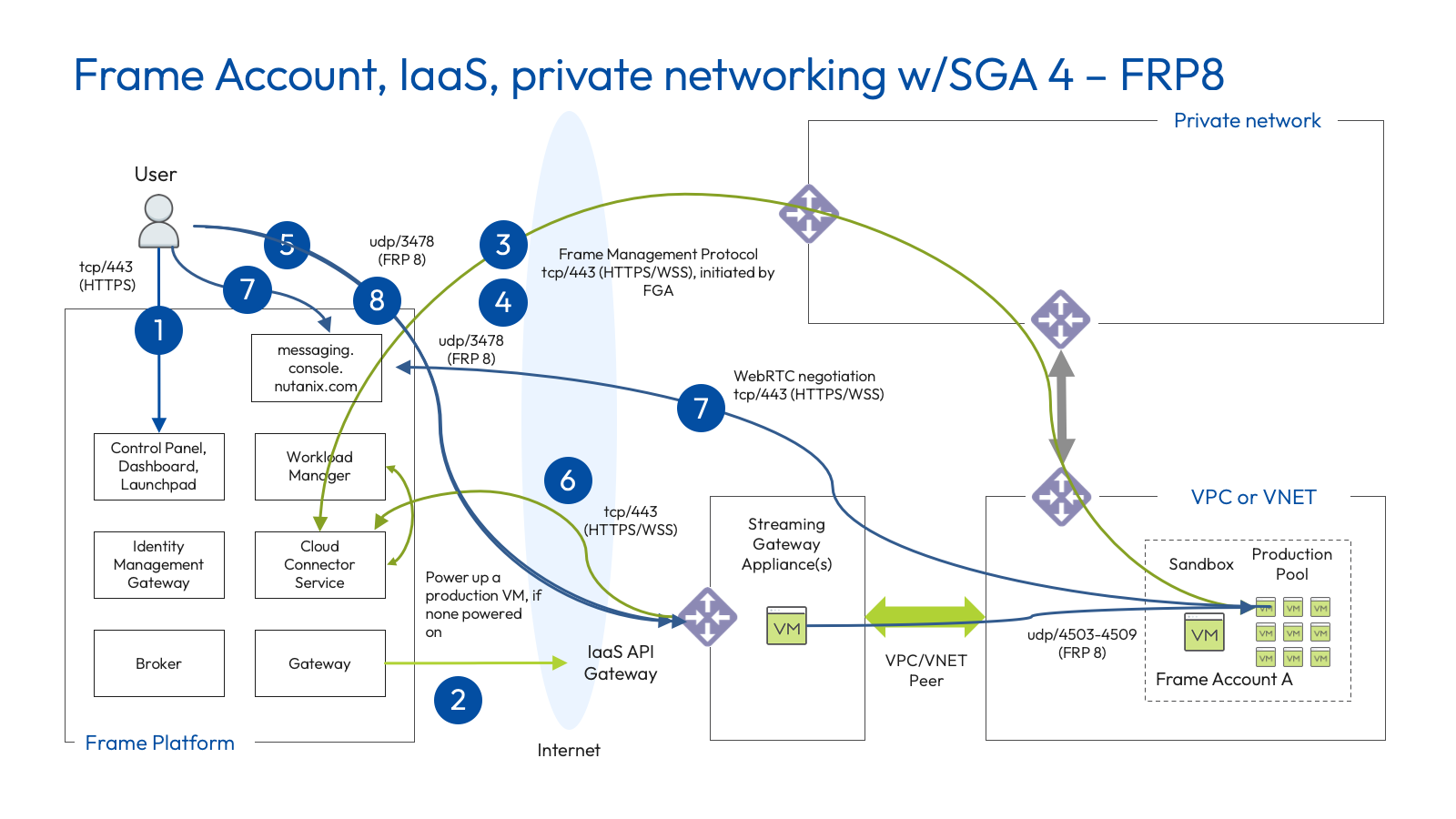
The following table describes the required protocols and ports for Frame accounts using Private Networking with SGA 4 and FRP8.
Dizzion is in the process of migrating from *.nutanix.com to *.difr.com domain. For the
time being, the additional difr.com domains will need to be whitelisted in addition to the
existing nutanix.com domains. At a later time, once Dizzion has confirmed there is no
dependencies on the nutanix.com domains, we will send out a communication notifying
customers that all nutanix.com domains can be safely removed from your whitelist
configurations.
IMPORTANT: For IMG Domains, Customers can whitelist new IMG difr domains but
should NOT change SAML 2 configurations to use new difr.com domains. SAML 2
configurations should continue to use img.console.nutanix.com and
img.frame.nutanix.com until further direction from Dizzion.
USE: Private Networking (Public Cloud) - Streaming Gateway 4
| Source to Destination | Source IP address | Destination FQDN(s) | Protocol/port |
|---|---|---|---|
| Workload VMs to Frame Platform | Public IP address |
|
tcp/443 (HTTPS) |
| Workload VMs to Frame Platform | Public IP address |
|
tcp/443 (HTTPS, WSS) |
| End user to Frame Platform | Public IP address |
|
tcp/443 (HTTPS) |
| End user to Frame Platform | Public IP address |
|
tcp/443 (HTTPS, WSS) |
| SGA VMs to Frame Platform | Public IP address |
|
tcp/443 (HTTPS, WSS) |
| End user to SGA VM | Public IP address |
|
udp/3478 and tcp/3478 |
| SGA VM to End user | Public IP address |
|
udp/49152–65535 |
| SGA VM to Workload VM | Private IP address |
|
udp/4503–4509 |
| Workload VM to SGA VM | Private IP address |
|
udp/49152–65535 |
FRP8 Networking (SGA 4)
The following table lists the required protocols and ports for Frame accounts using Private Networking with SGA 4 and FRP8, specifically for organizations electing to use Dizzion's EU control plane.
DEU: Private Networking (Public Cloud) - Streaming Gateway 4
| Source to Destination | Source IP address | Destination FQDN(s) | Protocol/port |
|---|---|---|---|
| Workload VMs to Frame Platform | Public IP address |
|
tcp/443 (HTTPS) |
| Workload VMs to Frame Platform | Public IP address |
|
tcp/443 (HTTPS, WSS) |
| End user to Frame Platform | Public IP address |
|
tcp/443 (HTTPS) |
| End user to Frame Platform | Public IP address |
|
tcp/443 (HTTPS, WSS) |
| SGA VMs to Frame Platform | Public IP address |
|
tcp/443 (HTTPS, WSS) |
| End user to SGA VM | Public IP address |
|
udp/3478 and tcp/3478 |
| SGA VM to End user | Public IP address |
|
udp/49152–65535 |
| SGA VM to Workload VM | Private IP address |
|
udp/4503–4509 |
| Workload VM to SGA VM | Private IP address |
|
udp/49152–65535 |
